Embarking on a journey that pushes the boundaries between technology and morality, the White Hat hackers have emerged as the unsung heroes of the digital world. Their dedication to safeguarding our online existence has become a beacon of hope in an age where cyber threats lurk around every virtual corner. With an unwavering commitment to justice, these modern-day knights armed with their keyboards have embarked on a noble quest to protect innocent users from the dark forces that exploit our vulnerabilities.
Through a unique blend of technical prowess and a deep understanding of human nature, these ethical hackers have donned their invisible armor to combat the ever-evolving landscape of cybercrime. Armed with their code of conduct, which they have sworn to uphold, they strive to strike a delicate balance between harnessing their skills for the common good and resisting the temptation that lies within the shadows. This tireless battle against the forces of chaos and malevolence illuminates a path towards a safer and more secure digital future.
Driven by a desire to expose the flaws that threaten our interconnected world, these cybersecurity crusaders traverse the intricate network of technologies and systems, unmasking potential cybersecurity vulnerabilities along the way. With every step they take, they expose the hidden truths that lie beneath the surface, shedding light on the importance of proactive defense measures. Meticulously dissecting the intricate webs woven by hackers, these guardians of the digital realm impart invaluable knowledge and insights, empowering individuals, businesses, and governments to fortify their defenses.
However, the path of the White Hat hacker is not without its challenges. It requires extraordinary discipline, constantly staying one step ahead of those who are determined to exploit system weaknesses for personal gain. The immense responsibility they bear forces them to navigate the boundary between right and wrong, their intentions always under scrutiny. Yet, motivated by a desire to make a positive impact, they prove that ethically wielding their skills can write a new chapter in our ongoing quest for a secure digital world.
Understanding the Code of Ethics of a White Hat Ethical Hacker

Exploring the principles and values that guide the actions of a white hat ethical hacker, we delve into the ethical framework that distinguishes their approach to cybersecurity. In this section, we examine the fundamental concepts and beliefs that shape the work of these skilled professionals.
The code of ethics of a white hat ethical hacker is rooted in a commitment to the responsible and legal use of their skills and knowledge. They employ their expertise to identify vulnerabilities within systems and networks, with the ultimate goal of strengthening security measures and safeguarding against potential threats. Through their meticulous efforts, they contribute to the protection of data, privacy, and the overall integrity of digital ecosystems.
- Integrity: Upholding the highest standards of moral and ethical conduct is central to the philosophy of a white hat ethical hacker. Their actions are driven by a dedication to honesty, transparency, and the protection of the public interest.
- Lawfulness: Adhering strictly to local and international laws, a white hat ethical hacker performs their activities within legal boundaries. They obtain proper authorization and consent before engaging in any security assessments or penetration testing.
- Confidentiality: Respecting the privacy of individuals and organizations is paramount for a white hat ethical hacker. They handle sensitive information with the utmost care, ensuring it remains confidential and is used solely for the purposes of vulnerability assessment and security improvement.
- Continuous Learning: The ever-evolving nature of technology necessitates that white hat ethical hackers continuously update their knowledge and skills. They actively engage in professional development, leveraging training opportunities to remain at the forefront of emerging cybersecurity threats and countermeasures.
- Responsibility: White hat ethical hackers acknowledge their responsibility to society and the larger digital community. They prioritize the greater good and act in a manner that benefits the security and stability of systems and networks, rather than exploiting vulnerabilities for personal gain.
In the next sections, we will delve into specific examples and case studies that exemplify the ethical mindset and practices of white hat ethical hackers, shedding light on their indispensable role in the realm of cybersecurity.
The Motivation behind Ethical Hacking
Exploring the underlying drive behind individuals who dedicate themselves to ethical hacking, also known as White Hat hacking, reveals a fascinating world of purpose and responsibility. These individuals possess a unique combination of curiosity, technical brilliance, and a strong moral compass. They are motivated by the belief that utilizing their hacking skills for the greater good can help safeguard digital spaces and protect against potential cyber threats.
Curiosity: The motivation to understand and dissect complex systems drives many white hat hackers. They possess an insatiable curiosity, always seeking to uncover vulnerabilities and weaknesses in digital infrastructure. This relentless pursuit of knowledge compels them to constantly refine their skills and stay one step ahead of potential adversaries.
Technical Brilliance: White hat hackers are masters of the digital realm, utilizing their extensive technical expertise to identify and exploit security vulnerabilities. Their deep understanding of programming languages, networks, and computer systems allows them to navigate intricate digital landscapes with precision. This unparalleled skillset enables them to craft innovative solutions to protect against evolving cyber threats.
Moral Compass: While hackers are often associated with illegal activities and breaching security, white hat hackers defy this stereotype. Driven by a strong moral compass, they are committed to using their skills for good. Their ethical code dictates that they leverage their expertise to help individuals, organizations, and even governments defend their sensitive information from malicious actors, thereby upholding privacy and cybersecurity for all.
The greater mission: Beyond personal gain or recognition, the motivation behind white hat hacking is a higher purpose. These individuals strive to make a positive impact by ensuring the safety and integrity of digital environments. By identifying vulnerabilities before they are exploited by malicious hackers, white hat hackers play a crucial role in preventing potential breaches and minimizing the impact of cyber attacks.
Unmasking the Hidden Side of Cybersecurity

In the realm of digital protection, a veil has been cast over an often overlooked aspect - the concealed side of cybersecurity that exists beyond the traditional notions of safeguarding. As we explore this captivating world, we begin to unravel the enigmatic layers and delve into the shadows where our understanding is challenged.
Within the realm of safeguarding online infrastructure and data, there lies a darker side that lurks in the depths, shielded from the majority's gaze. This clandestine aspect, like a hidden face behind a mask, demands our attention and invites us to explore its intricate complexities.
We venture beyond the white-hat ideals and explore the intricacies of the black-hat tactics, the shadowy underworld of hacking and illicit activities that exist in the cyber realm. The allure of this concealed world lies in its mastery of deception, manipulation, and exploitation, making it an essential area to comprehend for those striving for comprehensive cybersecurity knowledge.
Unmasking the dark side of cybersecurity allows us to gain insight into the methods utilized by hackers, the motives that drive them, and the vulnerabilities they exploit. Understanding these elements enables us to construct more robust defense mechanisms and cultivate a proactive approach in safeguarding our digital arenas.
Through this exploration, we detach the mask and shed light on the intricate dance between the attacker and the defender, unveiling the covert strategies employed on both sides. By grasping the tactics used by malicious actors, we arm ourselves with the knowledge required to not only protect but also anticipate and counter their moves.
In the realm of cybersecurity, knowledge is power. Unmasking the hidden side allows us to expand our horizons beyond the realm of white-hat ideals, fostering a deepened comprehension of the multifaceted world we strive to protect.
The Vital Role of Ethical Hackers in Safeguarding Digital Assets
In the rapidly evolving digital landscape, where cyber threats loom large, the protection of digital assets has become paramount for individuals, organizations, and governments alike. Amidst this ever-present danger, a group of individuals referred to as white hat hackers have emerged as the unsung heroes. Their dedication to maintaining the security and integrity of digital systems and assets has positioned them as the vanguard in the fight against cybercrime.
The role of white hat hackers, also known as ethical hackers, is multifaceted and essential in safeguarding digital assets from malicious activities. Unlike their nefarious counterparts, black hat hackers, white hat hackers deploy their extensive knowledge of computer systems and networks to identify vulnerabilities and potential threats proactively. Through various penetration testing techniques, these ethical hackers play a crucial role in exposing weaknesses in digital systems before they can be exploited by cybercriminals.
White hat hackers work closely with organizations and individuals, providing invaluable support in strengthening the security infrastructure of digital systems. By conducting thorough audits and assessments, these ethical hackers ensure that security measures are up to date and capable of withstanding sophisticated cyber attacks. They meticulously analyze coding and configuration, assessing the resilience of networks, and identifying any potential weak points that could compromise the integrity of digital assets.
Beyond their technical expertise, white hat hackers also play a vital role in educating and raising awareness among computer users about the significance of cybersecurity. Through workshops, seminars, and online resources, they impart essential knowledge on safe browsing practices, password security, and the importance of regular software updates, thus empowering individuals to protect their own digital assets.
The contribution of white hat hackers in protecting digital assets extends beyond individual organizations. They actively collaborate with law enforcement agencies and other cybersecurity professionals to share knowledge and combat emerging threats collectively. By reporting vulnerabilities and participating in bug bounty programs, white hat hackers help to identify and address security weaknesses in popular software and digital platforms, enhancing the overall security of the online ecosystem.
In conclusion, the indispensable role played by white hat hackers in safeguarding digital assets cannot be overstated. Their technical expertise, proactive mindset, and dedication to promoting cybersecurity make them the driving force in ensuring the protection of digital systems and assets. Through their continuous efforts, they strive to create a safer digital world for individuals, organizations, and governments alike.
The Evolution of Ethical Hacking Techniques
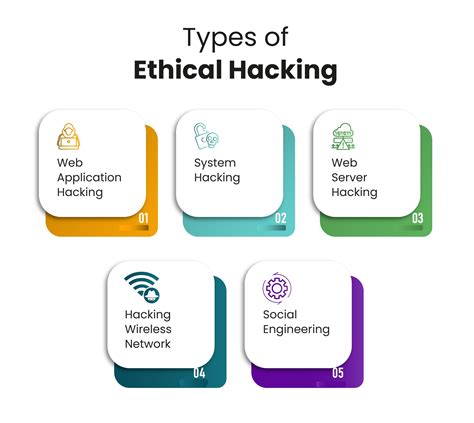
In the realm of cybersecurity, a fascinating transition has taken place over the years, as honorable individuals have emerged as champions of safeguarding digital systems. Through a series of innovative advancements, these skilled professionals, known as ethical hackers or white hats, have continually adapted their techniques to stay one step ahead of malicious actors.
The evolution of white hat hacking techniques can be traced back to the early days of computing, where the focus was primarily on reactive measures to detect and address vulnerabilities. However, as technology rapidly progressed, it became evident that a proactive approach was necessary to proactively identify and mitigate potential threats.
With the advent of social engineering and the increasing complexity of interconnected systems, white hat hackers have expanded their repertoire beyond traditional methods. They now utilize a diverse range of tools and strategies, including penetration testing, bug bounty programs, and vulnerability assessments, to uncover weaknesses before they can be exploited.
Moreover, as new technologies and trends emerge, such as cloud computing and the Internet of Things, white hat hackers are constantly refining their skills to keep up with the evolving threat landscape. They tirelessly explore novel attack vectors, study emerging attack techniques, and collaborate with fellow experts to develop robust defense mechanisms.
By combining technical expertise, analytical thinking, and an unwavering commitment to ethical principles, white hat hackers continue to push the boundaries of what is possible. Their tireless efforts not only ensure the security of digital infrastructure but also contribute to the advancement of cybersecurity as a whole.
The Legal and Ethical Considerations in Ethical Hacking
In the realm of ethical hacking, there are numerous legal and ethical considerations that must be taken into account. These considerations shape the landscape in which white hat hackers operate, ensuring that their actions are within the boundaries of the law and aligned with a strong ethical framework.
Legal considerations: White hat hackers must be fully aware of the legal implications associated with their actions. While they may have noble intentions, unauthorized access to computer systems, networks, and data can still be considered illegal in many jurisdictions. Understanding and strictly adhering to applicable laws and regulations is crucial to avoid potential legal consequences.
Ethical considerations: Unlike black hat hackers, white hat hackers operate with a defined set of ethical principles. They prioritize honesty, integrity, and respect for others' privacy rights while undertaking their activities. It is their responsibility to practice responsible disclosure, ensuring that vulnerabilities they discover are reported to the relevant parties promptly and discreetly, rather than exploiting them for personal gain.
Responsible disclosure entails informing affected parties of vulnerabilities without disclosing the information publicly, allowing them time to implement security patches or fixes. This approach safeguards the overall security of systems and ensures that potential attackers do not exploit the vulnerabilities before they can be patched.
Furthermore, white hat hackers must also consider the potential consequences and collateral damage that their actions may have. While their intentions may be noble, their activities can inadvertently disrupt systems or cause unintended harm. Therefore, implementing proper safeguards and conducting thorough testing before initiating any hacking activities is of utmost importance.
In conclusion, the field of ethical hacking is not just about identifying vulnerabilities and finding solutions but operates within a legal and ethical framework. White hat hackers must navigate these considerations, working within the boundaries of the law and upholding strong ethical principles to truly fulfill their role as defenders of cybersecurity and protectors of digital infrastructure.
Case Studies: Successful Ethical Hacking Stories

In this section, we delve into the fascinating realm of White Hat hacking by exploring a series of captivating real-world case studies. These stories shed light on remarkable instances where ethical hackers have used their skills to identify vulnerabilities and enhance security measures in various digital systems. Through their persistent efforts and astute problem-solving skills, these individuals have played a crucial role in safeguarding sensitive information and mitigating potential cyber threats.
One compelling tale showcases the accomplishments of an ethical hacker who was able to uncover a critical flaw in a prominent social media platform's encryption algorithm. By meticulously analyzing the code and employing innovative techniques, the hacker successfully thwarted a potential data breach, preventing the unauthorized exposure of millions of users' personal information. This case study serves as a testament to the invaluable role that White Hat hackers play in safeguarding the privacy and security of online platforms.
Another noteworthy case study revolves around a team of ethical hackers tasked with assessing the vulnerability of a financial institution's network infrastructure. Through a combination of penetration testing, vulnerability scanning, and social engineering, they identified and promptly patched several vulnerabilities that could have led to devastating cyber attacks. Their proactive approach and meticulous attention to detail highlight the significance of ethical hacking in the constantly evolving landscape of cybersecurity.
Furthermore, we delve into the remarkable achievements of a White Hat hacker who collaborated with a healthcare organization to uncover a potential data leak in their patient records system. By harnessing their technical expertise and exceptional problem-solving abilities, they successfully identified and remediated the security flaw, preventing the exposure of sensitive medical data. This case study emphasizes the importance of ethical hacking in the healthcare sector, where protecting patient privacy is of paramount importance.
These are just a few examples of the many success stories within the domain of ethical hacking. Through their tireless dedication and commitment to enhancing cybersecurity, White Hat hackers continue to play a pivotal role in fortifying digital systems, safeguarding sensitive information, and ensuring the overall safety of individuals and organizations in the digital age.
Embarking on the Path to a Rewarding Career: White Hat Hacking Certifications
In today's digital age, where cybersecurity threats loom large, the demand for skilled professionals proficient in ethical hacking continues to rise. The realm of white hat hacking, also known as ethical hacking, presents aspiring individuals with a promising opportunity to embark on a lucrative and fulfilling career.
Obtaining white hat hacking certifications serves as a crucial stepping stone towards achieving the knowledge and skill set necessary to combat cyber threats effectively. These certifications validate an individual's expertise in ethical hacking methodologies, tools, and best practices, equipping them with the necessary credentials to pursue various roles within the cybersecurity industry.
White hat hacking certifications provide a comprehensive education on the principles of ethical hacking, including vulnerability assessment, penetration testing, and network security. By pursuing these certifications, professionals gain invaluable practical experience in identifying and resolving security vulnerabilities, safeguarding confidential information and systems from unauthorized access, and conducting ethical hacking assessments to fortify organizational security.
- CEH (Certified Ethical Hacker): This certification equips individuals with a broad understanding of ethical hacking techniques and tools, imparting knowledge about the mindset of hackers and enabling them to anticipate potential security breaches.
- CISSP (Certified Information Systems Security Professional): A globally recognized certification, CISSP covers a wide range of cybersecurity domains, including ethical hacking, emphasizing the application of best practices and techniques to protect sensitive data.
- OSCP (Offensive Security Certified Professional): Designed for hands-on learners, the OSCP certification focuses on practical skills and requires candidates to successfully exploit vulnerabilities in real-world scenarios.
- GPEN (GIAC Penetration Tester): This certification validates a professional's expertise in penetration testing methodologies and tools, enabling them to evaluate network security and identify potential weaknesses.
White hat hacking certifications not only provide individuals with a competitive edge in the job market characterized by a growing demand for cybersecurity experts, but they also serve as a testament to their commitment to upholding ethical standards in the field. These certifications open doors to a variety of rewarding career opportunities in cybersecurity consultancy, penetration testing, security auditing, and more.
Embark on the journey towards a thriving and impactful career by obtaining white hat hacking certifications, as they pave the way for a future where your expertise can safeguard individuals, organizations, and industries from malicious cyber threats.
Exploring Tools and Resources for Aspiring Ethical Hackers

Embarking on the journey to become a white hat hacker can be an exciting and challenging pursuit. Acquiring the necessary skills and knowledge to protect against cyber threats requires the right tools and resources. In this section, we will delve into a range of valuable assets and technologies available to aspiring white hat hackers.
1. Penetration Testing Frameworks: One of the most essential tools for a white hat hacker is a reliable penetration testing framework. These frameworks provide a structured approach to simulating cyber attacks and identifying vulnerabilities in computer systems and networks. Popular frameworks include Metasploit, Burp Suite, and OWASP ZAP.
2. Network Scanning and Vulnerability Assessment Tools: Assessing and analyzing network security is a crucial aspect of ethical hacking. Network scanning and vulnerability assessment tools help identify weaknesses in a network's infrastructure, detect open ports, and uncover potential entry points for hackers. Notable tools in this category include Nmap, OpenVAS, and Nessus.
3. Password Cracking Tools: As a white hat hacker, understanding password security and attempting to crack passwords is an important skill to possess. Password cracking tools aid in testing the strength of passwords, uncovering weak or reused passwords, and evaluating overall password security within an organization or system. Well-known tools in this domain include John the Ripper, Hashcat, and Hydra.
4. Security Blogs and Websites: Staying up-to-date with the latest trends, techniques, and vulnerabilities is essential for any aspiring white hat hacker. Engaging with security blogs and websites provides invaluable insights, news, and educational resources to enhance knowledge and skills. Some notable sources to explore are KrebsOnSecurity, Dark Reading, and SecurityWeek.
5. Virtual Labs and Capture the Flag (CTF) Challenges: Hands-on experience is crucial for honing hacking skills. Virtual labs and CTF challenges provide safe environments for practicing ethical hacking techniques, solving puzzles, and mastering different aspects of cybersecurity. Platforms like Hack The Box, TryHackMe, and OverTheWire offer various challenges to put skills to the test.
By utilizing these tools and resources, aspiring white hat hackers can gain the necessary expertise to protect against cyber threats, contribute to the improvement of overall cybersecurity, and forge a successful career in the field of ethical hacking.
Exploring the Future of Ethical Hacking and Cybersecurity
The realm of ethical hacking and cybersecurity is constantly evolving, with new trends and innovations shaping the way white hat hackers protect digital systems and networks from malicious activities. In this section, we will delve into the exciting future landscape of ethical hacking, highlighting key trends and advancements that will play a vital role in safeguarding digital assets from cyber threats.
- Artificial Intelligence (AI) Integration: As technologies become more sophisticated, the integration of artificial intelligence into cybersecurity practices is expected to rise. AI-powered systems can quickly analyze vast amounts of data and identify potential vulnerabilities, allowing white hat hackers to proactively defend against attacks.
- Internet of Things (IoT) Security: As IoT devices continue to permeate our daily lives, ensuring their security becomes paramount. White hat hackers will play a crucial role in testing and identifying vulnerabilities in IoT devices, guaranteeing the privacy and integrity of connected systems.
- Blockchain Security: With the increasing adoption of blockchain technology, ensuring the security of digital transactions and decentralized ledgers will be a focal point for white hat hackers. Collaborative efforts will be made to address potential vulnerabilities and enhance the overall security of blockchain networks.
- Cloud Security: As organizations migrate their infrastructure and data to the cloud, the challenges of securing cloud services become more complex. White hat hackers will continue to develop innovative techniques to assess and fortify cloud security, protecting sensitive information stored in cloud environments.
- Biometric Authentication: With the rise of biometric authentication systems such as fingerprint recognition and facial recognition, white hat hackers will concentrate on uncovering vulnerabilities that could potentially compromise these advanced security measures. By identifying weaknesses, they can assist in strengthening biometric authentication systems.
- Threat Intelligence: The proactive identification and analysis of potential cyber threats will become an integral part of white hat hacking techniques. By staying ahead of emerging threats and constantly monitoring the digital landscape, white hat hackers can provide invaluable insights to organizations, enabling them to enhance their cybersecurity defenses.
As the digital world continues to expand, the role of white hat hackers and the field of cybersecurity will become increasingly important. By embracing these future trends, ethical hackers can ensure the integrity, privacy, and resilience of our digital infrastructure, creating a safer and more secure online environment for individuals, businesses, and society as a whole.
FAQ
What is the article "Unveiling the Dream of the White Hat" about?
The article "Unveiling the Dream of the White Hat" discusses the concept of white hat hacking, which refers to ethical computer hacking aimed at enhancing cybersecurity.
Are white hat hackers legal?
Yes, white hat hackers are legal. They are individuals who use their skills and knowledge to identify vulnerabilities in computer systems with the owner's permission, in order to improve security.
How does white hat hacking help enhance cybersecurity?
White hat hacking helps enhance cybersecurity by proactively identifying vulnerabilities and weaknesses in computer systems before they can be exploited by malicious hackers. This allows organizations to patch and fix these vulnerabilities, thus preventing potential cyber attacks.
What distinguishes white hat hackers from other types of hackers?
White hat hackers are different from other types of hackers, such as black hat hackers, because they use their skills to protect and secure computer systems rather than misuse them for personal gain or to cause harm.
How can someone become a white hat hacker?
To become a white hat hacker, it is important to have a strong understanding of computer systems and network security principles. Acquiring certifications and participating in ethical hacking programs and activities can also help develop the necessary skills and knowledge.



